Malware behavior analysis
Malware behavior analysis using Microsoft Attack Surface Analyzer.
Intro
To do an interactive malware behavior analysis a few tools are needed. I mention “interactive” because the idea is not to just throw a malware sample into a sandbox but analyse the malware using a Windows VM and monitor the behavior that way. A few tools I would use to do so are the following:
Regshot to detection registry changes
Wireshark to detect network behavior
Process Monitor to detect various API calls like WriteFile
Recently a new Version of Microsoft Attack Surface Analyzer was published and I wanted to find out what the idea and purpose of this tool is.
“Attack Surface Analyzer is a Microsoft-developed open source security tool that analyzes the attack surface of a target system and reports on potential security vulnerabilities introduced during the installation of software or system misconfiguration.” - Microsoft Attack Surface Analyzer.
The idea is to take a snapshot prior the installation of the software and then to take another snapshot after the installation. The tool will then display changes based on which the engineer or auditor can decide if a security risk exists or not.
The tool is able to display the following changes:
File system (static snapshot and live monitoring available)
User accounts
Services
Network Ports
Certificates
Registry (Windows only)
Analysis
As these artifacts are also very interesting to a malware analyst I thought it might be a good idea to use the Attack Surface Analyzer to analyze malware. To verify this idea I copied the software into my malware analysis lab.
The first thing I had to do was taking a snapshot of the clean machine. The user interface is pretty basic and looks as follows:
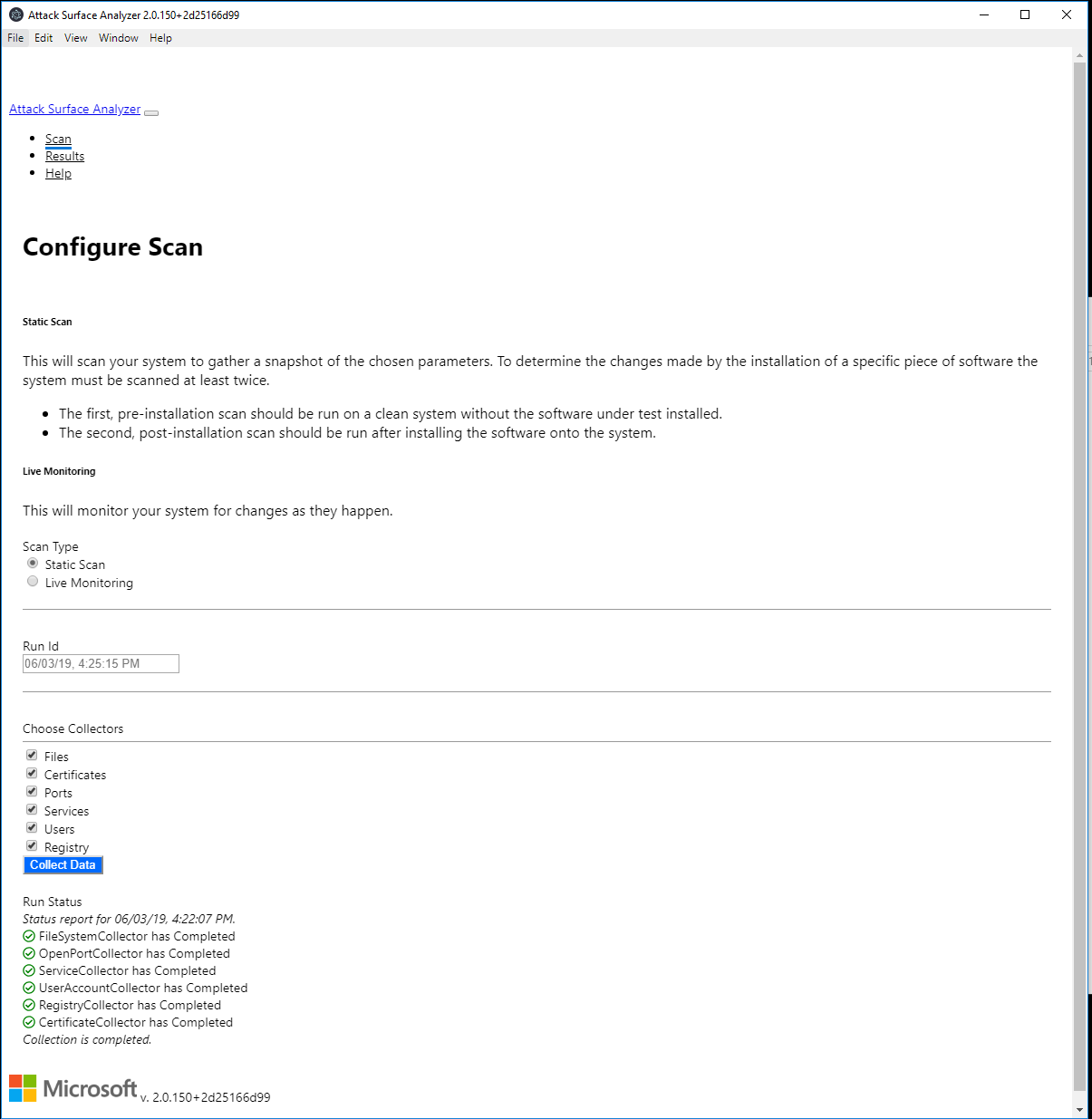
After taking the first snapshot I executed the malware which made various changes on my machine. To find out what kind of changes were made I took another snapshot using the Attack Surface Analyzer. As soon as this process is finished I’m able to compare the two snapshots using the “Results” button in the tool. The page changes and the user can choose two different snapshots and run the analysis.
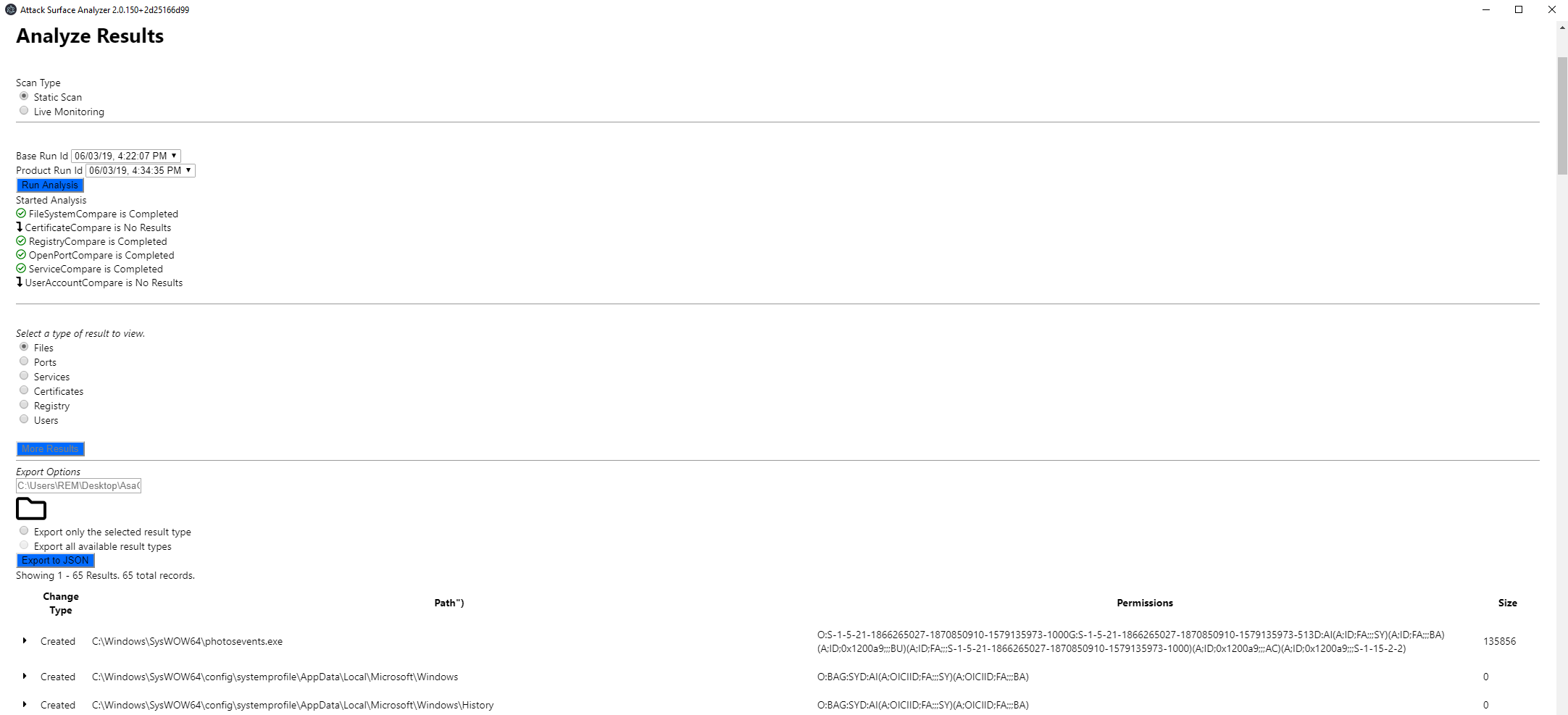
As soon as the analysis is finished the user can select the type of artifact he would like to compare. In the following picture I compared the files and can see that a file called “photosevents.exe” was created. Using the other artifact types the analyst can also see that a new service with this name was created and obviously also e registry entry for this service exists.
Conclusion
So is this tool a good alternative to all the other available tools to do “interactive” behavior analysis of malware?
In my opinion this tool gives a slight overview what a malware does. But with just monitoring these artifacts it is mostly only possible to detect the persistence mechanisem. Detecting other malware behavior like process creations, injections, short network connections and so on.. is not possible with this tool. At least not yet.
Therefore if I have to do a malware analysis I will stick to the multiple tools which I mentioned in the beginning. But as I’m not very experienced in malware analysis I’m very welcome for other opinions and other good tool suggestions.